NETWORK ACCESS CONTROL
Keep risky devices away from network resources with real-time network visibility
Get real-time network visibility and prevent risky BYOD, IOT, and other devices from accessing network resources.
Why should you deploy Network Access Control?
With the increasing number and type of devices accessing your network, it is important to provide visibility of all devices and where they are on the network. This prevents non-compliant or risky devices from accessing your network or applications. NAC solutions enable complete policy and device life cycle management.
What happens if I do not deploy a Network Access Control solution?
Without a NAC, it’s difficult to have confidence that you know everything on your network, can block unauthorized access, and all devices are secure. It’s also much more challenging to demonstrate compliance with internal policies and external regulations.
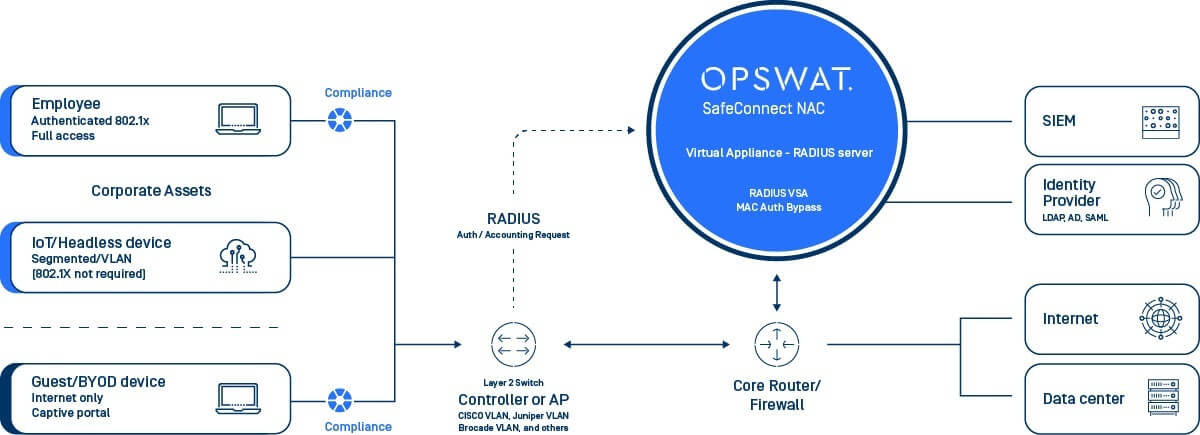
How Network Access Control Works?
Device profiling and visibility Discover user and IoT (Internet of Things) devices as they attempt to access the network. Devices can be profiled in a passive manner or quarantined until the device is explicitly known using rich patterns and advanced heuristics.
| Guest and BYOD Networking access Control access for any type of device (BYOD, managed devices, IOT devices). The captive portal allows different authorization and access levels based upon user groups, including guests.
|
Deep endpoint compliance and real-time posture check Ensure every device is compliant with a wide range of policies. Integrates with OPSWAT Endpoint Security SDK technology, which is the most widely used technology for checking device security and compliance in the industry.
| Incidence responseTake in threat information from an IDS/IPS and act on severe threats to block compromised devices instantaneously.
|
Seamless Integration Leverage device information, including user ID, IP and MAC addresses, role, location, time and ownership of the device. This information is called Contextual Intelligence and can be published tomany security solutions, such as firewalls and Security Incident and Event Monitoring systems (SIEMs).
|
|



